My wife, Kerry, went down to California last thanksgiving for a brief trip with her sister Sandy. They were driving along in Fountain Valley with my niece and spotted a kitten lying in the gutter. As they approached her she hauled herself out of the gutter in a badly injured way.
They immediately stopped and tried to get the kitten out from the bush she’d crawled into. The neighbors said she’d been hiding in that bush for at least 2 days. Animal control had been out and couldn’t catch her.
It took the three of them 45 minutes to get her out with my wife crawling under the bush coaxing her the whole time. She eventually caught the little thing and they took her to the Vet ER.
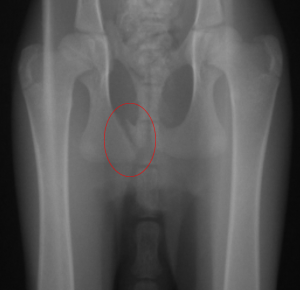
Turns out Stix, as she came to be called, had a broken pelvis. She was 9 weeks old. Three breaks, with the largest one highlighted on the xray below. This xray links to the hi-res full body xray if you’re interested.
Kerry and Sandy had to leave immediately to drive back to Colorado from California and they took Stix with in a cat carrier.
Stix was paralyzed from the base of her tail down and Kerry was told the kitten may not be able to use the bathroom properly. On the drive back to Colorado, in a Vegas hotel room the first time Stix peed in the catbox there were cheers. Later that night she pooped, and more cheers. In that hotel room when Kerry cleaned her cat carrier the blanket was covered in dead fleas that had fallen off from the anti-flea medication the vet gave her. She also wolfed down her first meal like she was starving.
Kerry started by saying she’s just going to foster her and find her a good home once she’s recovered. The road to recovery was long. Kerry kept her in a cat carrier initially. As she healed she bought a large pet playpen and kept her in there to limit her movement. She recovered further and eventually got to roam around the house supervised.
Of course attachments grew and she became our cat.
The first time she lifted her paralyzed tail slightly was a big day. A few months later we were watching TV with her and she actually twitched the end of her tail and we were shocked. More cheers.
It’s now 9 months later and she’s the new favorite child of our three pets. We have an australian cattle dog and Stix doesn’t realize she’s a cat. She imitates our cattle dog so much we’ve called her a cattle-cat. When Joey chases the ball, she goes after him. And she follows us around when we take Joey for a walk. That’s in between wrestling with our oversized orange tabby.
This is a video of her at the end of a 20 minute walk in 90 degree heat out here in Colorado. She’s very camera shy so it’s taken me a while just to get this footage. I’ve never known a cat that comes when you call her. She’s awesome and for starting life with a broken pelvis she’s turned into a great hiker and runner which is highly unusual for a cat.
Our cattledog has always been partial to me – they tend to be a one person animal. When Kerry is sitting reading, Stix will jump on her chest and snuggle right under her chin. So she jokes she finally has a pet of her own.
Not all rescues have a happy ending like this and the prognosis for Stix was very bad when Kerry and Sandy rescued her. But I see similar stories online and I think animals are tougher than humans because they don’t know that they’re injured or disabled and so they lack self-pity. As far as Stix is concerned, everyone else’s tail is just a little too active and for some reason in the last few months her back legs got all grasshoppery and now she just wants to run everywhere.